PDF) Progression of right atrial and ventricular size with increased right ventricular systolic pressure: A review of 5412 cases of pulmonary hypertension | Darryl Burstow - Academia.edu
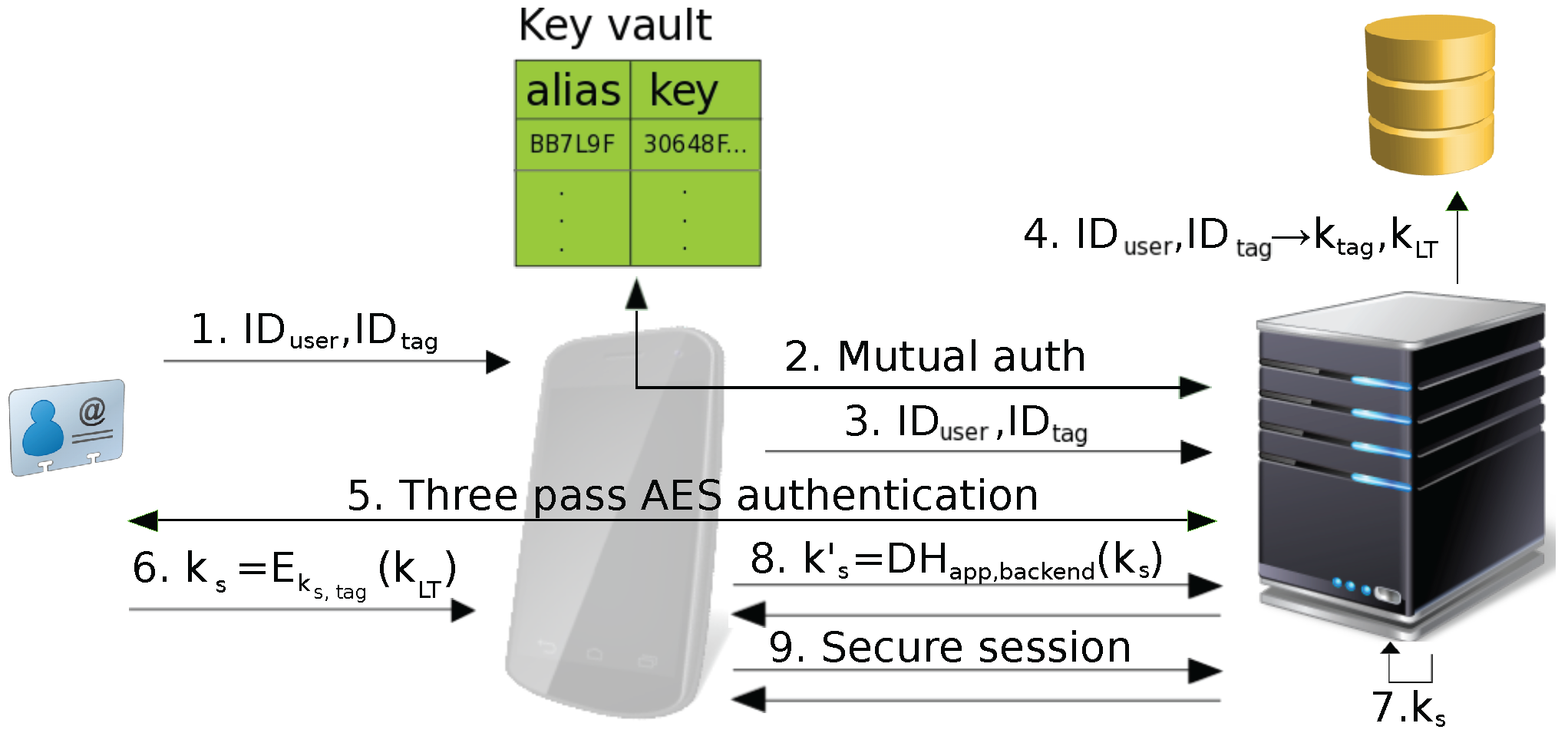
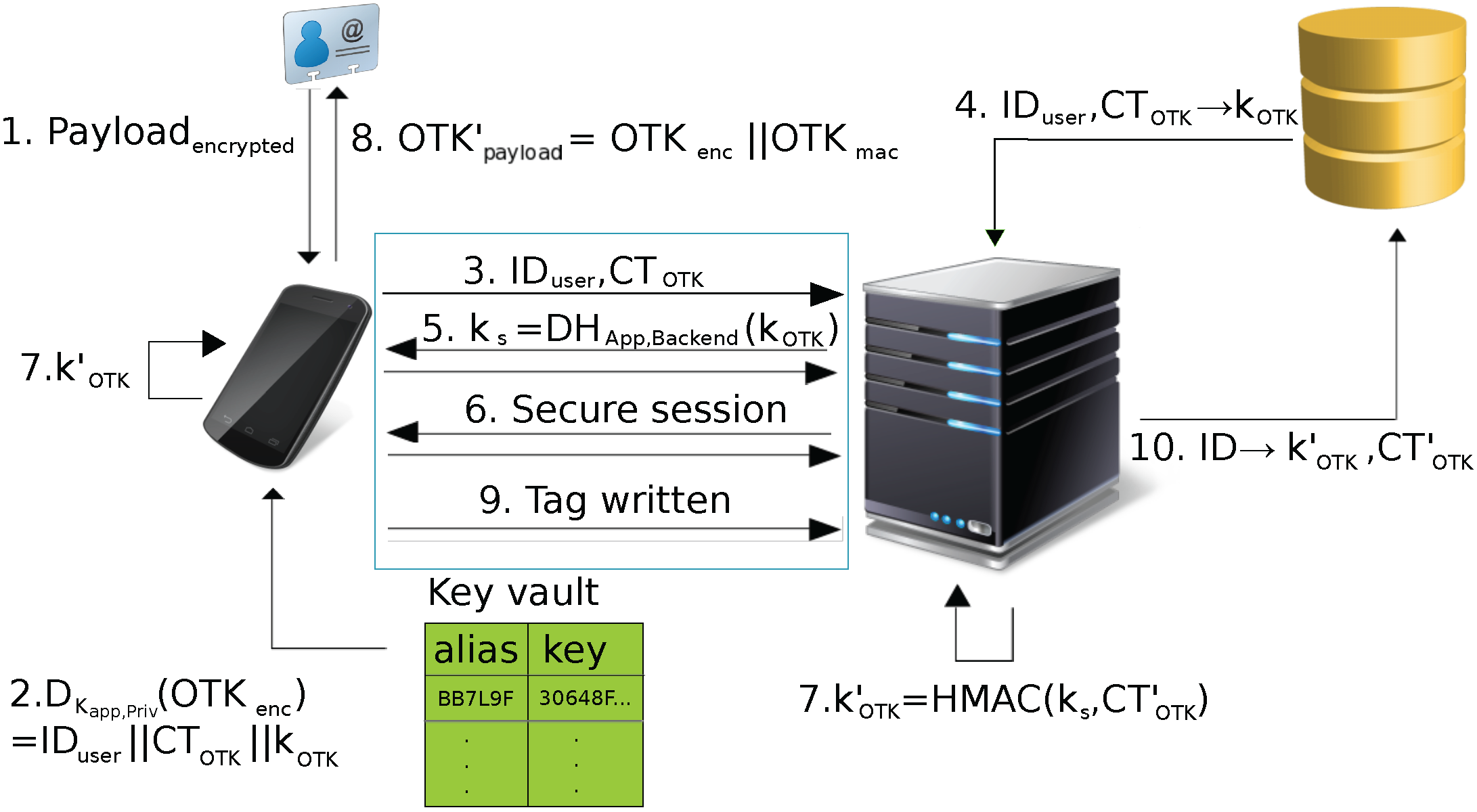
Information | Free Full-Text | Protecting Touch: Authenticated App-To-Server Channels for Mobile Devices Using NFC Tags | HTML
BOBUm, 11 JTARCH, 1913. Ul'SERAIi CR3SKS ITO^ 33, I . CHANGES BCX ASSiailMEi^TS, •i/^ SDJ^fk.X©avlng changes of respon'sa and